We know, it’s sad. You missed our mobile attribution webinar last week. We missed you too!
But we have a solution. Two of them, in fact.
First, if you missed our “No BS Mobile Attribution Webinar” last week, it is still available on-demand. We had fun doing the webinar, and we think you’ll enjoy listening to it as well. But second, if you don’t have 30 minutes to spare, it might be faster to read the answers we provided here.
First, a quick recap: content & speakers
Mobile attribution can be confusing, and it can seem pretty detailed and technical sometimes. That’s why we hosted the attribution webinar with friends from Vungle and Liftoff. And we had three experts, who are also providing the answers you see here …
Barbara Mighdoll
Senior Director of Marketing
Singular
David Bennett
Sales Engineer
Liftoff
Rina Matsumoto
Performance Optimization Lead, US
Vungle
OK. The mobile attribution webinar questions (and answers)
1) What is mobile attribution?
Rina: Mobile attribution is the way mobile marketers understand from which marketing channels their app users are acquired.
It’s incredibly important to know which traffic sources are bringing not only users but high LTV users into your app. This will allow you to invest your marketing budget in the right sources.
2) From Andrew at Flipboard: “Can you please touch on challenges and capabilities for tracking attribution from a mobile app?”
Barbara: Well, this is a fairly broad question that could be taken in so many directions, and since we are just starting the discussion I’ll keep this high-level.
Mobile attribution at the core is the bridging together of advertising and mobile technologies. The challenge to attribution is being able to keep up with this constantly evolving technology, and I’ll also add the constantly evolving ecosystem threats like fraud. However, when done right, the insights from mobile attribution allow marketers to execute and evaluate their mobile marketing campaigns with proper app conversion metrics.
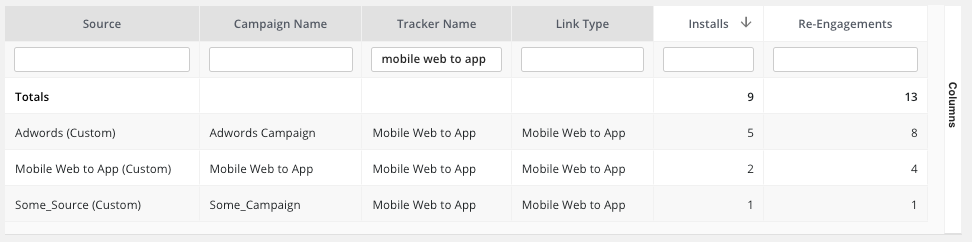
2) What are tracking links? How do they work?
David: There are multiple types of tracking links, impression tracking links and click tracking links. These links are used to gather data around what partners are driving impressions and clicks for you. They also allow us to track what users are downloading your app after seeing an ad.
This helps you assign attribution.
The tracking links also help us route users to the App Store, the Google Play store, or other app marketplaces. In the case of re-engagement or retargeting campaigns they can also be setup to route users directly to your app. In general, they make data collection for digital marketing possible.
As for how they work, they send information to your MMP when impressions are shown or when ads are clicked. The information that they send contains device data as well as a few other key pieces of information. Since they contain device data it allows you to track when users are installing your app because of your advertising efforts and what actions they are taking in your app because of your advertising efforts.
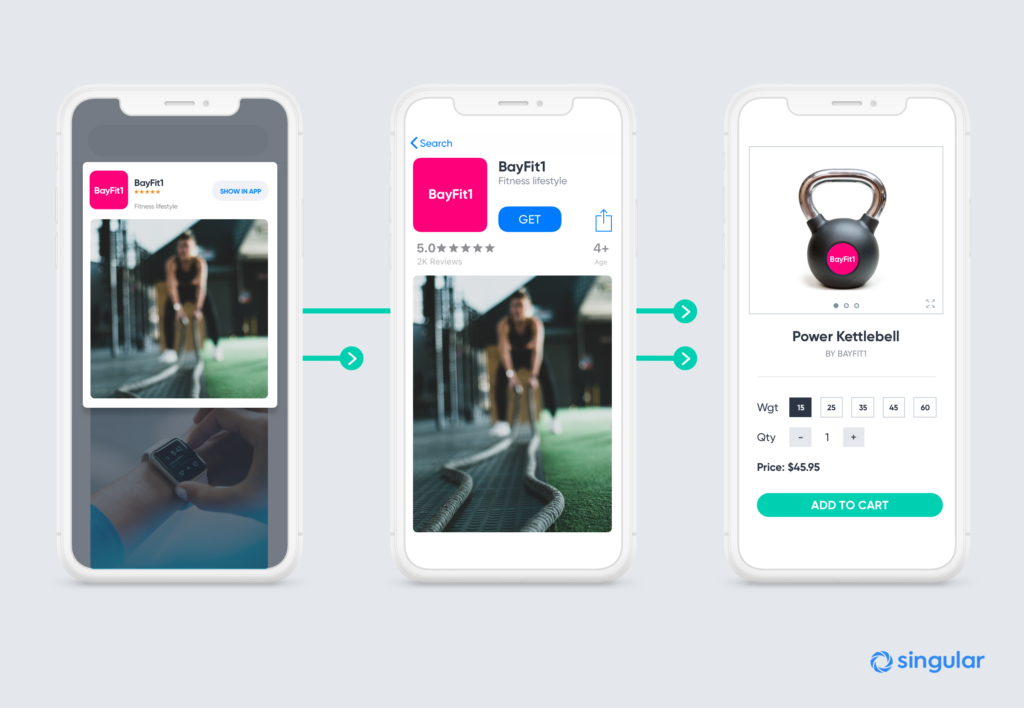
3) What is deep-linking? Why does it matter?
David: Deep-linking is a technology that allows you to link to your app directly from your ads [editor’s note: whether in an app or on the mobile web]. For re-engagement campaigns this means a smoother user experience.
This is important because it allows you to minimize the number of steps that your users have to complete in order to reach the desired event. This usually leads to better performance and increased ROI.
Barbara: Just to add a quick comment here, I think this technology has become a pretty standard part of an attribution stack, and because of that most users now expect when they click on an ad with a particular CTA, the app will open in the correct location.
3) What are postbacks? Should I be getting them?
Rina: Postbacks are the way networks receive in-app data from clients, whether that’s installs or post-install events like in-app purchase or tutorial completion.
These postbacks will be key depending on your network’s buying model or optimization methodology. So it’s important to consult your network partners on what postbacks they’ll be needing.
David: This enables you to share user behavior with your advertising partners.
4) What is a SAN?
David: Self attributing networks such as Facebook, Google, and Twitter inform your attribution partners which installs and actions they drove.
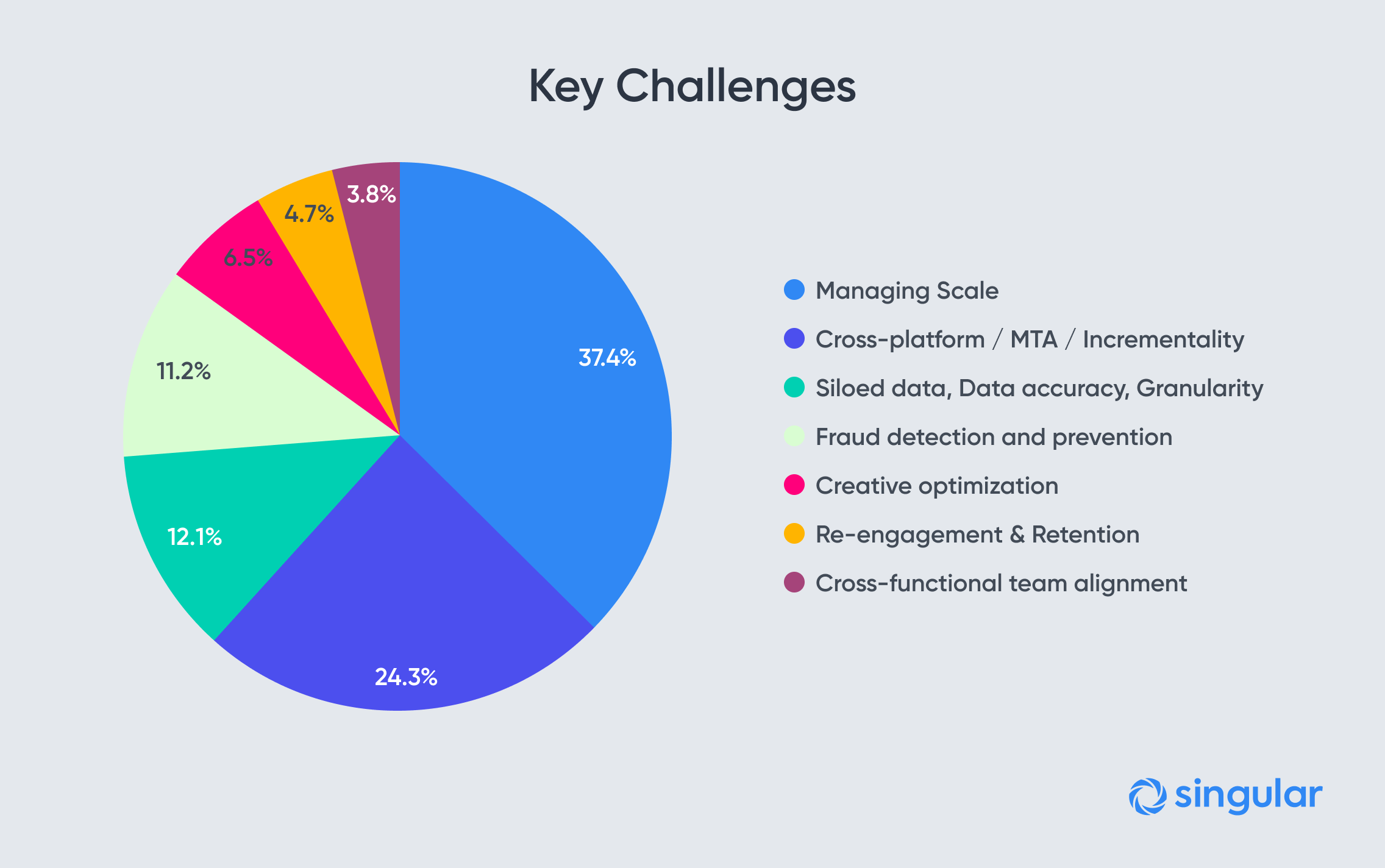
5) What is granularity? Why do marketers need granularity?
Barbara: Granularity describes how deep a marketer is able to analyze their data.
For example, basic granularity usually includes drilling down to the app & source level, while sophisticated marketers are able to go deeper into the campaign, publisher, keyword and even creative levels. With this level of detail, marketers can decide when they should shift budget. They also can better inform how to spend their time optimizing – and know exactly where to optimize.
Advanced marketers who have been able to achieve scale and see massive growth are the ones who are able to optimize at deep levels of granularity. For example, as part of our Marketing Intelligence Platform we offer creative reporting where we are able to pull in your ad creative so you can easily match your data to your ads.
One of our customers who started utilizing these creative level insights saw ROI increase 40% within 2 months.
Rina: I agree with Barbara. Granularity helps you understand what types of users were acquired and how they were acquired. Are these users from iOS 11? Were they acquired from a specific type of creative?
It’ll also help in investigating any issues with discrepancies and potential campaign or fraud issues, by being able to drill down to specific parameters.
6) Why do marketers need to combine customer-level mobile attribution data and campaign-level marketing data?
Barbara: This is a great question, and one that we address frequently because the complexity of this is often misunderstood.
Before I jump into the why marketers need to combine this data, I first want to touch on why combining it is even a challenge.
Marketing data is only available in aggregate like ad spend, while attribution data is available at the user-level like app installs. By nature, aggregate and user-level data do not fit together – it’s like trying to assemble a puzzle with pieces from different sets.
This means that marketer’s datasets are often left incomplete and inaccurate. Left this way, marketers do not have the ability to dig into granular levels of insights. And this is a core problem Singular solves – we redefined how attribution data matches campaign data with the experience we’ve acquired over 4 years of mapping this ecosystem.
So to answer why marketers need to combine these two datasets, the answer is pretty simple: to unlock ROI at granular levels like the campaign, publisher, keyword and creative-levels.
Rina: User level data are data points like device type, OS version, and country. Campaign level data are data points like publisher and creative information. Only once you marry this data do you have a full understanding of your marketing campaigns.
7) Can I see where ad networks are running my ads? If so, how?
Rina: At Vungle, we try to provide as much transparency to our advertisers as possible. We share publisher site names with all of our clients to give full transparency into their campaigns.
This transparency allows advertisers to better understand their user base and buy more intelligently on our platform.
8) What are the most critical reporting needs in mobile attribution?
Barbara: First of all, discrepancy and transparency are critical. No matter how your attribution provider is getting install and cost data (i.e. via API or tracking links), there are bound to be discrepancies between your provider and your ad networks. Being able to analyze these discrepancies is extremely valuable to avoid making decisions based on incorrect data.
Shameless plug:
One of the advantages of using Singular, is we allow you to compare data sets side by side without having to toggle between dashboards. And using our transparency feature, marketers can select their preferred source for each metric, then easily locate discrepancies in their data, while even setting-up alerts when discrepancies exceed a threshold.
In addition, ROI (return on investment) is the single most important metric for mobile marketers. However, most attribution providers are only able to provide ROI insights at the source level because they are unable to reliably match cost and campaign data with user level data. True ROI data empowers you to optimize your advertising by the quality of users it’s driving, instead of just install and revenue data. It’s also a must-have if you want to scale your programs while maintaining or even improving efficiencies.
David: In my experience at Liftoff, when there are some discrepancies in between different reports the first two places that we would look are fraud and tracking issues. If the discrepancy is due to fraud we revamp what we are doing and work hard to protect our customers.
If the discrepancy is caused by tracking issues we work with our customers and their attribution providers to get tracking functioning as expected.
9) What kinds of ad fraud are most common? How can I avoid them?
Barbara: Today there are two main forms of fraud: fake users and attribution manipulation. Fake users involves bots, malware and install farms to emulate clicks, installs and in-app events, causing advertisers to pay for activity that is not completed by a real user.
Attribution manipulation is an especially dangerous form of fraud since it not only costs marketers their spend but also corrupts performance data, causing marketers to make misguided acquisition decisions. The two most common types are click injection and click spamming.
David: Click fraud is a major form of fraud that we are seeing right now. It can be anything from click farming to click spamming to click injection to ad stacking. These types of fraud are meant to drive a high number of clicks, reduce the CPC of a campaign and possibly steal attribution from users that could convert organically.
Another example of fraud would be install-fraud through something like install farming or click spamming to steal install credit. These types of fraud are done to drive a higher number of installs to reduce the CPIs of a campaign. In order to combat both click-fraud and install-fraud Liftoff recommends focusing campaigns on actions that users perform through CPA goals or KPIs or through setting ROAS goals or KPIs.
Other ways that we help our customers avoid fraud are blacklisting suspicious traffic, blacklisting traffic from suspicious sources, we even go so far as to reject anonymous traffic, or traffic that doesn’t have advertising IDs or IP addresses associated with the devices.
10) How can I avoid ad fraud?
Rina: Attribution partners and ad networks will have their own technology to prevent and detect fraud.
Something that you can do as an advertiser is take a look at ROAS data, which can be useful to spot install fraud or fake users. However, click fraud or attribution manipulation will typically snipe organic users that usually have high LTV.
At Vungle, we recommend marketers take a closer look at their CTR/CVR and click to install time distributions to find any anomalies. Any abnormally high CTR or low CVR can signal that the clicks aren’t real. A click-to-install time distribution that is skewed beyond the one hour mark is also an indicator that most users didn’t download after a real click that redirected them to the store.
11) Should I pay extra for fraud protection?
Barbara: The biggest mistake marketers can make is to think that fraud is a “nice to have” feature, or that they can “block fraud manually”. Even traffic that looks great i.e. good retention, high ROI can actually be fraud due to attribution manipulation. That’s why we at Singular offer fraud prevention for free.
Also be careful of the actual type of fraud prevention your provider has. With fraud costs so high and growing every year, you need to ensure that your attribution platform not only detects fraud but proactively prevents fraud in real-time.
And by this I mean some attribution providers do not offer actual prevention, but only detection. That means they offer “alerts.” where you then have to manually look at the data and fix it in retrospect. Be on the lookout for prevention types including IP blacklists, geographic outliers, hyper engagement, install validation, and time to install analysis – and the more included the better.
12) How can I ensure brand safety in my mobile advertising?
David: We have customers that worry about brand safety and focus on targeting specific verticals and avoiding others. This is done by setting up either blacklisting or whitelisting for specific types of apps. An example of this would be to blacklist violent apps.
13) Getting app installs is great, but it’s just the first step. What are the most important post-install events to measure?
David: App marketers need to determine which post-install events are the best indicators for future conversions and revenue. Once these events have been determined, these become the events that should be tracked and used to set goals for your campaigns.
These events might be adding an item to your cart or reaching level ten in a game. The idea is that these events indicate a high LTV.
Rina: Understanding short-term metrics as a proxy to determine long-term LTV is the key for performance marketing.
Often times ROAS in the short term is strong indicator of high LTV.
If users often monetize later in their user lifetime, looking at other benchmarks like level completions or retention could be the solution for campaign optimizations.
14) Data is critical to mobile marketing success. Why do I need API access to my attribution partner’s datastream? What kinds of data should I have access to?
Barbara: One of the critical elements to pay attention to if you are in the search for a new attribution provider is data accessibility. After all, your data is only valuable if it’s readily available and in a usable format. This is especially important for marketing organizations with centralized internal reporting.
Regarding what kinds of data you should have access to, there are two types:
- Aggregate
This includes LTV, retention, or other in-app KPIs grouped by any number of segments (app, media source, campaign, ad ID, etc).
- User-level/device-level
Why do you want this? Just one example: you may need to join that device-level data with offline or proprietary data and perform internal analysis on that combined dataset.
15) Do I have to use one attribution solution across all my apps?
David: The short answer is no … but the long answer is a lot more complicated but really comes down to how many tools you want to worry about integrating and how many tools you want your employees to have to learn.
The more attribution solutions you use across your portfolio the more complexity you add to your portfolio.
Barbara: Yes, complexity is the issue. Do you want to have multiple dashboards? Different workflows?
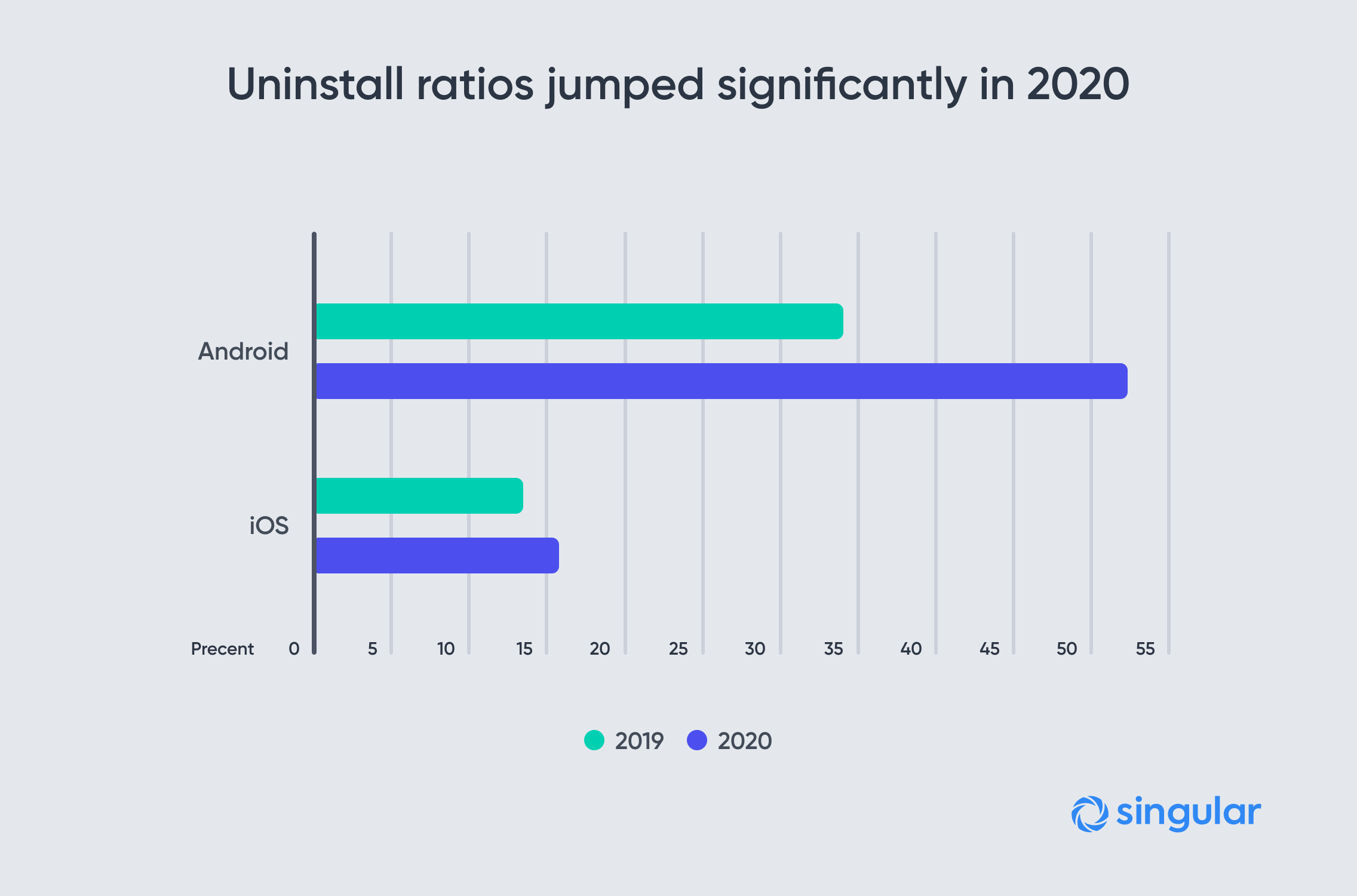
16) Measuring installs is great, but we do have attrition. How important is uninstall measurement?
Barbara: Uninstall measurement is a useful metric when it comes to understanding your users.
Uninstall data by itself is interesting, but its best used in conjunction with other lower-funnel events to understand the behavior of your users and of your marketing activities.
Aside from the insights, uninstall data can be provided to partners to be used in campaigns for retargeting audiences.
17) Can I use attribution to know how much ad revenue I’m generating from each mobile app user? Or from each network?
Rina: Analytics providers are starting to develop features to ingest ad revenue data to be able to track true LTV of acquired users. As ad revenue on the user level data becomes more readily available, I expect this feature will be widely used by developers.
Barbara: The short answer is yes. It’s a developing technology that we have some customers using right now. The best thing I can say is … talk to us!
Next steps: mobile attribution master class
Quick-witted readers may be wondering: How did 27 questions turn into 17? The answer: via the magic of multiple queries within each one.
But you may still have unanswered questions.
The solution: get a copy of our 7 things your mobile attribution tool doesn’t do (but should) report! Alternatively, get a full demo of Singular’s mobile attribution capabilities.