What is SKAdNetwork?
SKAdNetwork (StoreKit Ad Network) is a framework, a set of software and protocols created by Apple for privacy-safe mobile attribution for user acquisition campaigns. SKAdNetwork, or SKAN, allows marketers to get deterministic but aggregated attribution of mobile app marketing campaigns. That means marketers know which advertising campaigns worked and what marketing channels are performing, but it’s still privacy-safe: they don’t get device-level data on what individual people are doing.
Apple made SKAdNetwork essentially mandatory for mobile marketers in iOS 14.5 and on.
First, App Tracking Transparency (ATT) required apps to ask permission to access their app users’ IDFAs so they could track ad campaign effectiveness. Then, Apple made it clear that an alternative form of mobile attribution known as fingerprinting — tracking users by following their semi-unique device signatures around the internet — was never kosher: with or without tracking authorization via ATT.
Read on for all the details …
More than 5 years ago, in May 2018, Apple introduced a new concept and API called SKAdNetwork.
That API would allow mobile app install attribution while preserving privacy. At that time, many questions were raised about the future of mobile attribution on iOS and the place of SKAdNetwork in it. But with iOS 14.5, Apple made massive updates to SKAdNetwork and released SKAN 3, the first version that became functionally useful for mobile attribution. The updates to App Tracking on iOS in April of 2021 manifested in the AppTrackingTransparency framework and Apple’s new privacy guidelines.
In 2022, Apple further updated SKAdNetwork with the launch of version 4, commonly referred to as SKAN 4. And at WWDC 2023, Apple announced SKAN 5, which will offer the ability to attribute re-engagements. There are no further details about SKAN 5, however, and we don’t know exactly when it will become available.
SKAN 4 is much more capable than SKAN 3, with several key differences:
- Privacy thresholds became crowd anonymity, which should reduce null values in install postbacks
- Campaign IDs became source identifiers, providing more insight into campaigns that work
- 1 postback became 3 postbacks, offering more insight into quality and cohorts
- Postbacks became separated into two types: fine and coarse. The first postback can be fine, which offers 64 different potential values. The second and third postbacks are coarse: 1 of only 4 possible values.
- Timing changes, with marketers able to lock postbacks when a significant conversion event happens and get earlier data
- Web-to-app support
- Conversion values can decrease as well as increase in SKAN 4
(See a full SKAN 3 to SKAN 4 conversion guide right here.)
Singular has been preparing to utilize SKAdNetwork for a long time, and we made those plans a reality very early. We still get many questions from customers and partners who want to learn more, and we’ll continue to update our blog with multiple series to explore how SKAdNetwork works, what kind of data points it provides, and how it can be used for marketing measurement.
In this post, I will try to keep things high level.
What does SKAdNetwork do?
SKAdNetwork is a framework for privacy-preserving mobile install attribution. It aims to help measure conversion rates of app install campaigns (CPI) without compromising users’ identities.
You might be asking yourself how it achieves that and the key to understanding that is that Apple, and as an extension, the App Store itself is serving as a facilitator. The whole attribution process is actually conducted by the App Store and attested by Apple’s servers. It is then disconnected from user identifiers and temporal information and sent off to the network.
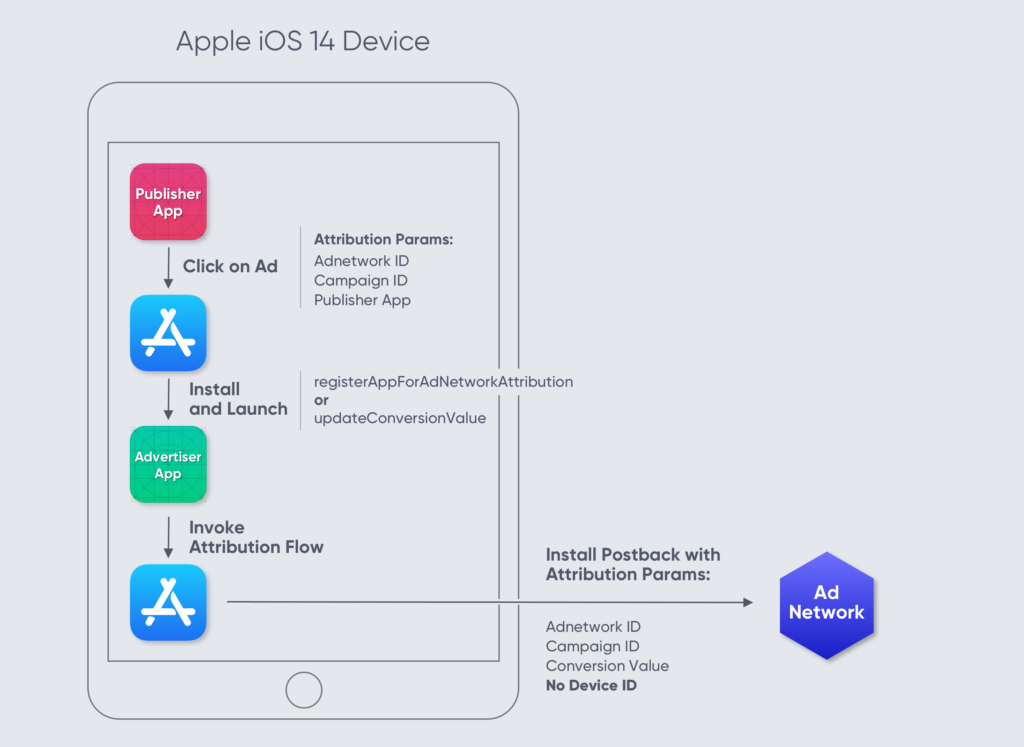
How does it work?
Simple … (well, not really, but we will try to simplify it)
When an ad is clicked and the store is opened, the publishing app and the network provide it with some basic information such as network, publisher, and campaign ID. The App Store will then send a notification of successful conversion to the network. It will report the attached values alongside a conversion value that can be reported by the advertised app.
That notification will be sent at least 24 hours after the first launch and will be devoid of any device or user identifying information. Additionally, the App Store conducts the process so the advertised app has no knowledge of the original ad and publisher. In such a way, the network receives an attestation that an install has happened, without tying the install to a specific user, thus preserving privacy.
With SKAN 4, which is still being implemented throughout the adtech ecosystem, marketers can also get a second and a third postback, providing more insight into how installs from certain campaigns are doing over time. The 3 postbacks, however, are not connected via an identifier or any other key: any cohort insights must be modeled.
What to expect when using SKAdNetwork install attribution
First, let’s cover what you get:
- Click-through attribution for ads displayed in mobile apps.
- Publisher ID of the publishing app, supporting full visibility and transparency into publishers.
- Under SKAN 3
- Campaign ID which is limited to 100 values and can be used to code any other campaign information (outside of publisher) such as campaign, creative, and placement.
- Under SKAN 4
- Source identifier which — at high levels of crowd anonymity — can provide 4 digits of information on campaign, creative, ad set, geo, and so on
- Under SKAN 3
- SKAdNetwork will tell you if this is the first time the user installed the app or not (is it a redownload).
- Under SKAN 5 (announced by Apple at WWDC 2023)
- SKAdNetwork will add the ability to attribute re-engagements with people who already have your app installed.
- Under SKAN 3
- Conversion Value, which is a number between 0 and 63 that can be set by the advertiser after a conversion happens, allows basic post-install tracking (for example, it can be used to show the highest level the user got to in the first day of playing). That value’s purpose is to give some estimates to the users’ quality.
- Under SKAN 4
- The first postback offers the same 0 to 63 number for what is now called a fine conversion value, if you achieve sufficient volume per campaign
- Apple has added 2 additional postbacks with conversion payloads that are coarse: 1 of only 3 possible values
- Apple’s cryptographic, unforgeable verification of the attribution and parameters. This is important, as it means anyone can verify that an install really happened without compromising user privacy.
- Accurate and mostly fraud-free attribution.
Now, to what you don’t get:
- View-through attribution wasn’t initially supported, but Apple has since added some limited capability for view-through attribution
- Click-through attribution for all ads displayed in a browser, email campaigns, and any other media apart for native ads
- Note though, that Apple added support for web-to-app measurement in SKAN 4. It is only for mobile Safari, however, so desktop and Chrome and Firefox and Brave (etc!) are not supported.
- Real-time data
- Notifications are sent to the network after 24 to 48 hours. Any subsequent update to the conversion value will postpone the notification. (Notifications are sent 24 to 48 hours after the app opened or the latest update to the conversion value). Apple is doing that to deter attempts to tie in the notifications with app activity to identify users.
- Under SKAN 4, the second and third postbacks have even longer postponements.
- User-level data: notifications do not include user identifiers.
- Data on small campaigns or publishers: Apple will send notifications only after a certain amount of conversions happened for the same publisher app and campaign ID. Apple does not publish what the privacy thresholds in SKAN 3 or the crowd anonymity in SKAN 4 levels are, nor does Apple specify how this count is actually being done.
- Advanced attribution services such as deferred deeplinking and long cohorts / LTV.
- Though you can get these via Singular’s SKAN solution, with some modeling.
Getting the most out of SKAdNetwork as an advertiser
As an advertiser, you must be asking yourself what’s the best way to utilize this mechanism that Apple has created.
Here’s a short checklist of the must-haves:
- You’ll need your media partners to support it by correctly integrating with the SKAdNetwork API. You’re mostly covered here for SKAN 3, and the ecosystem is building support for SKAN 4 now. Expect that to be fairly widespread by late summer 2023.
- You’ll also need to collect and validate, either yourself or with a vendor, the cryptographically signed install notifications from each and every media partner, in order to identify any issue or misuse. The goal here is to make sure everyone is telling the truth, and no funny business is going on. While we would all like to believe that everyone’s telling the truth, we also know that you can never be too safe, for the same reason that self-reported numbers should not be trusted. (Of course, your MMP — Singular — does all this collecting and validating for you.)
- Next up is analytics and reporting, to make sense of it all. The SKAdNetwork API provides a limited set of values and identifiers, which poses a challenge, yet not an impossible one. This is where smart encoding would help you maximize the amount of information you can pass via Apple’s API.
For example, Campaign IDs can be valuable but must be selected intelligently. You’ll want to ensure that the way that Campaign IDs are assigned is consistent across your channels and is supporting your reporting. (Singular provides super-simple ways to encode SKAN 3 and SKAN 4 campaign and conversion information.) - Intelligent parameter selection can also make a difference in optimization and post-install measurement. Having only 64 values (represented by 6 bits) for conversion information is limiting, yet a lot of information can be encoded using these 64 values if used smartly. For example, users can be categorized based on first-day activity to create segments that would later get grouped and evaluated for performance. You will need an automated way of assigning and tweaking these values without requiring dedicated Engineering work for it, so you’ll likely want a tool that can manage them, and tie it back to your reports.
Measurement partners such as Singular are well-positioned to support this whole process, starting with media partner integrations and assuming the central role in verification, analytics, and reporting. Here at Singular, we’re pretty confident that we provide the best possible solution for implementing SKAdNetwork, and the above are the foundations we have built into that solution.
Interestingly, we see this move as a natural progression of Singular’s product.
Singular’s unique position and unique integrations with media partners allow us to make the most out of this new API and enable our customers a fluid, seamless transition into this new age. We will work tirelessly to make sure our customers can utilize all the tools that are available to them.
Join our Mobile Attribution Privacy (MAP) group on Slack to exchange ideas and ask questions about these new privacy measures.