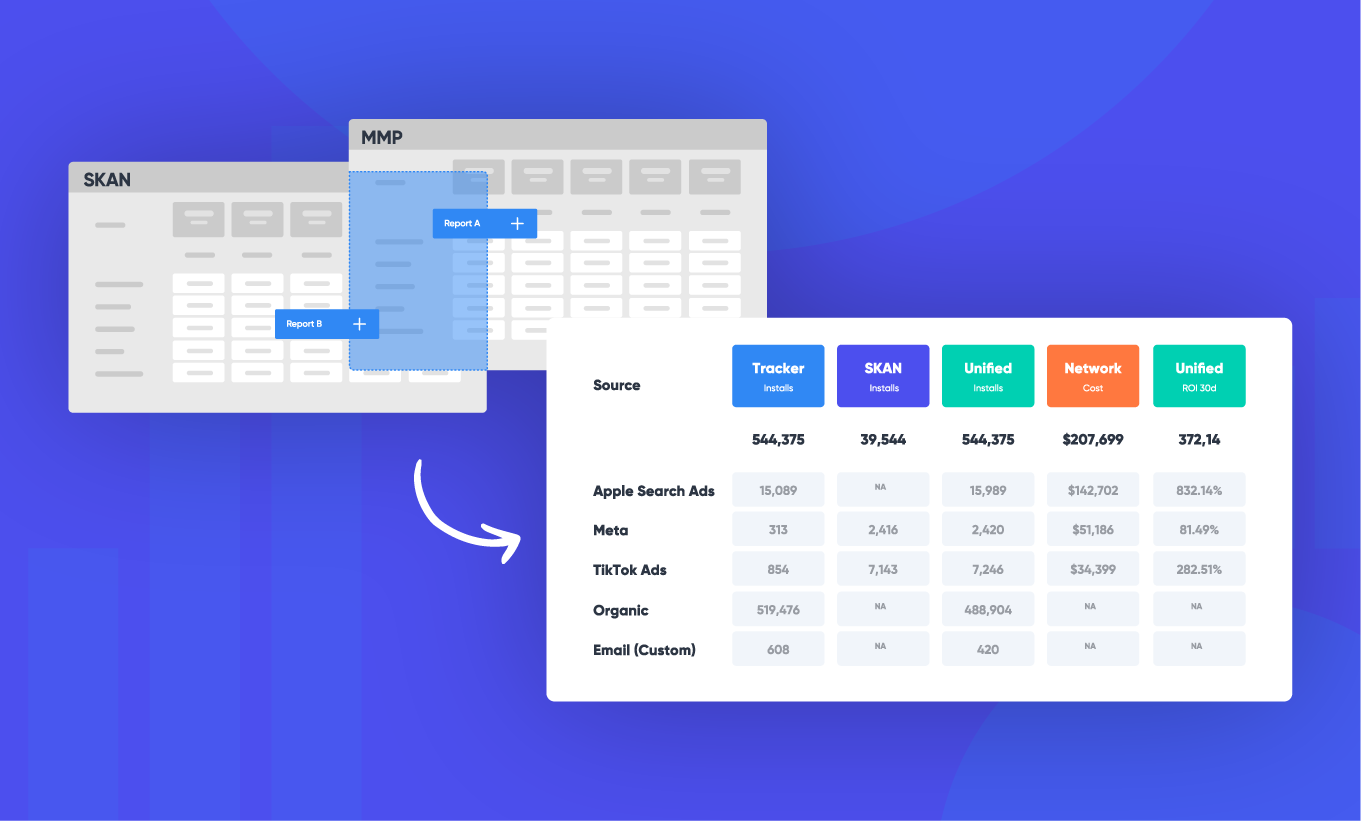
Attribution
Fixing iOS attribution
4 mins read
News & trends
TikTok has the most complete public ad library: Mozilla report says
3 mins read
Growth
Growing mobile apps in 2024: 5 ways app makers are winning despite challenges
7 mins read
News & trends
Women in growth: celebrating 5 inspiring leaders
6 mins read
Creative analytics
How to leverage custom product pages for your app or game
8 mins read
Attribution
Singular’s iOS Unified Measurement boosts accuracy 31%, providing true organics, accurate CPIs, 35-day cohorts
7 mins read
Ad monetization
Ad spend growth: app verticals that are growing over the last 6 months
3 mins read
Analytics
Multiple breakdowns: how to get more data from your ad networks than they offer (sort of)
3 mins read