Wondering what Apple’s new privacy enhancements mean for you?
Watch our on-demand webinar iOS 14 & IDFA Changes: What you need to know
Quietly rolled out by Apple on March 29th, 2018 with their iOS 11.3 release, SKAdNetwork is an API that validates advertiser-driven mobile app installs. In Apple’s documentation, it’s stated that SKAdNetwork’s objective is to help marketers to measure the success of an ad campaign while maintaining user privacy.
What’s different about the SKAdNetwork API?
SKAdNetwork is a class that belongs to the StoreKit framework; Apple’s In-App Purchase Payment System that manages transactions for In-App Purchases. After installing the app, Apple shares only 5 items with the advertiser: ad network ID, transaction identification, ad campaign ID, app ID installed, and attribution code to link all.
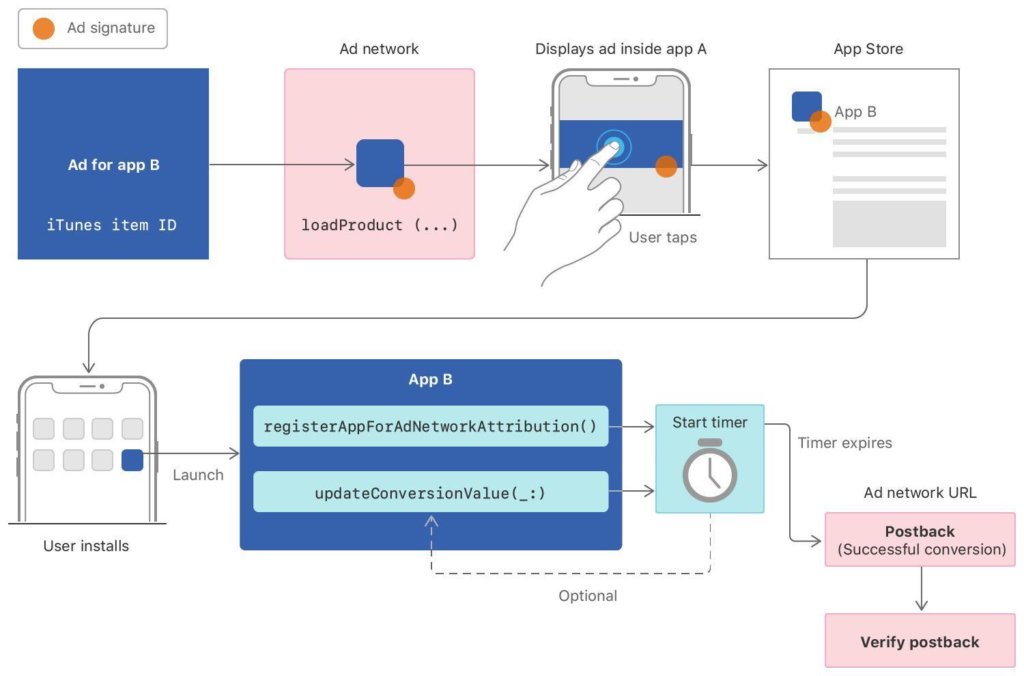
Source: Apple Developer Documentation
There are two key postbacks associated with SKAdNetwork:
- Initiating Install Validation: This Informs an ad network when users install and launch an app after viewing an ad. Ad networks initiate validation by providing signed information, including a campaign ID, when displaying the ad. Later, if the ad results in a conversion, Apple notifies the ad network with a postback that includes the same campaign ID.
- Verifying an Ad Conversion: When a user installs and launches an app as a result of your ad, you receive a postback request that validates the installation. The request is sent to the ad network URL provided in registration.
What does this mean for advertisers?
It’s still too early to predict how SKAdNetwork will play out. Adding to the mystery, Apple has been very hush-hush about their motives and the rollout of SKAdNetwork. However, we think there are a few possible ways this could play out:
1. Apple doesn’t actively push SKAdNetwork, it doesn’t garner significant adoption, and nothing changes in the mobile marketing space.
One possible scenario could be that Apple doesn’t actively push SKAdNetwork to advertisers, resulting in minimal adoption. In this scenario, there wouldn’t be any significant change in the way that app marketers manage their attribution.
2. Apple pushes SKAdNetwork and Google follows suit with their own version.
Another scenario is that Google follows suit with its own version of the ad network API. This scenario could play out a few different ways:
- Apple and Google don’t build out a robust attribution solution, which results in a lack of adoption by app marketers. Apple has made its mark in the world thanks to being an extraordinary and innovative hardware company, but they have never been accountable for providing analytics and insights to app marketers. If Apple and Google do not develop all the features that are necessary for an end-to-end attribution solution, (e.g. data extraction, all postback types, flexible attribution windows, easy BI integrations) then the industry will not adopt their solutions.
- Apple and Google develop all the functionality needed for a robust attribution solution, leaving third-party mobile app attribution providers to potentially die-off in their current form. Who can compete with the operators of the mobile app stores we attribute from anyway? However, advertisers may still lose out in this scenario because they might encounter more complexities coming from running attribution on two separate platforms. The winners in this scenario would be third-party mobile app attribution providers that offer value-added services such as connecting multiple networks into a single view and aggregating all necessary features into a single API.
3. Apple pushes SKAdNetwork but Google does nothing.
In a third possible scenario, Apple could actively push SKAdnetwork to advertisers, while Google doesn’t follow suit with their own version. This would still result in complexities for advertisers who would need to manage attribution programs in silos across different OSs.
In this scenario, marketers would turn to attribution providers who could help them gather data from multiple sources, standardize it, and aggregate it into a single ROI dashboard.
So what’s going to happen?
It’s unfortunately too early to say, but one thing is clear: Apple wants to enhance users’ privacy. Apple has clearly positioned itself as a top privacy-conscious company and will continue to hold this stance as data privacy becomes more top-of-mind in the industry.
